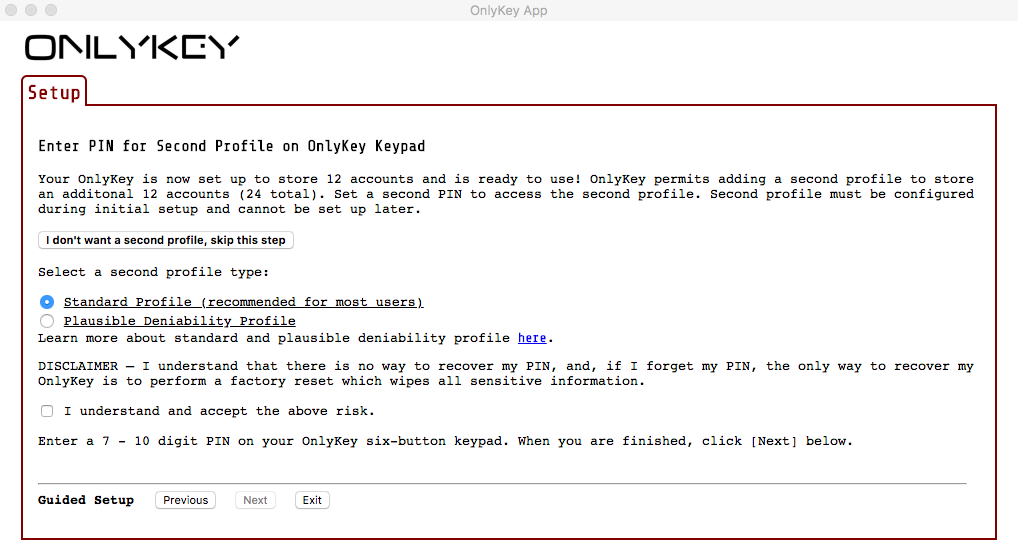
About Plausible Deniability
Before setting up plausible deniability read the International Travel Edition Guide here. Once enabled, an OnlyKey with the Standard Edition firmware that is in plausible deniability mode is identical in functionality to an OnlyKey with the International Travel Edition (ITE) firmware. Since the ITE firmware has only one profile and does not utilize any data encryption a user may if forced to unlock their OnlyKey, unlock the plausible deniability profile. It is then plausible that the user’s OnlyKey only has this one profile (the standard profile essentially becomes a hidden profile), and it is plausible that the user is not in possession of a data encryption device (useful where encryption my be banned as the ITE firmware does not encrypt any data).
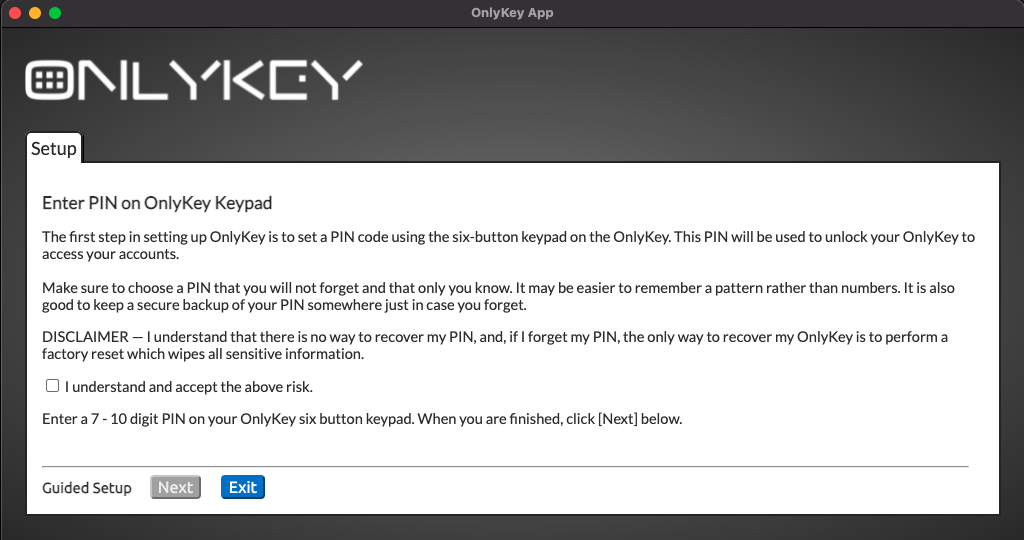
Steps to Setup Plausible Deniability
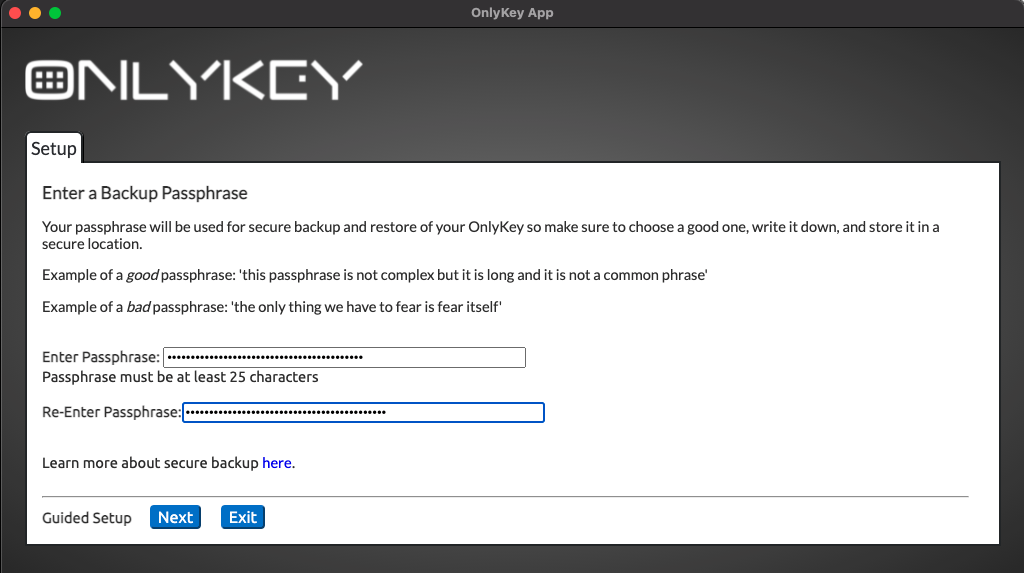
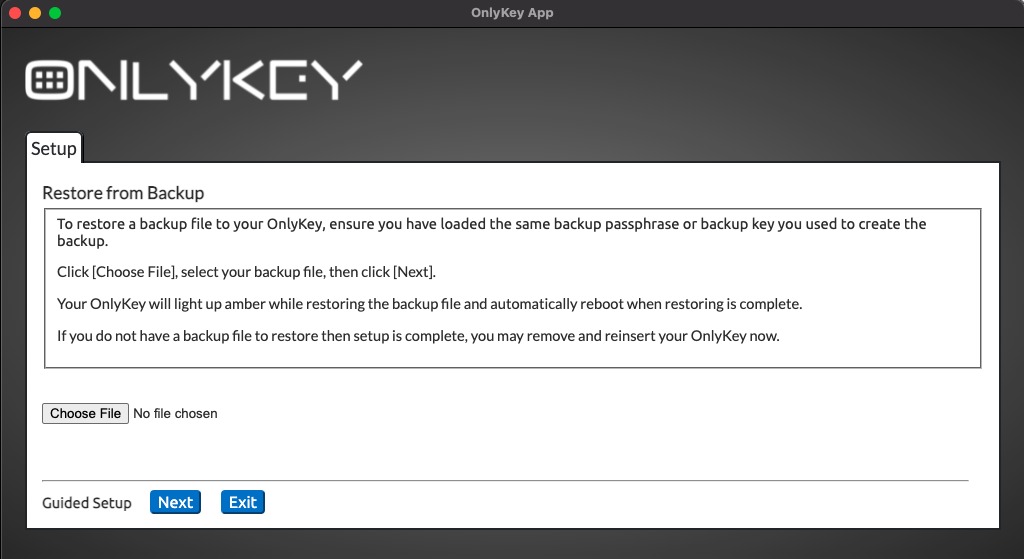
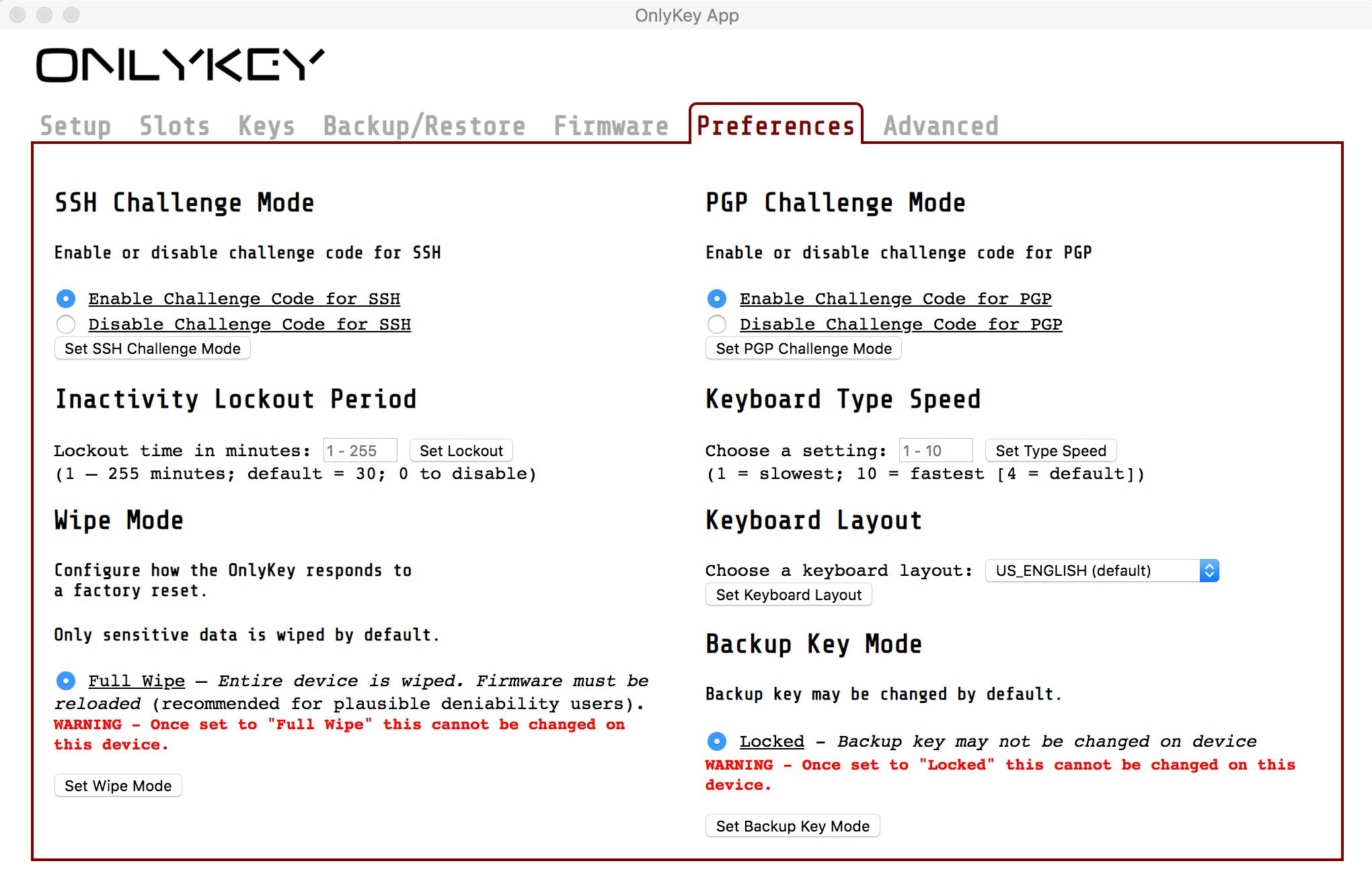
Plausible Deniability FAQ
Q - Is it believable that my OnlyKey only has one profile (only 12 slots used)?
A - We sell quite a few International Travel Edition (ITE) Onlykeys so yes it is believable that you are using one of these. It is also believable that even if you purchased a standard OnlyKey you then followed the guide here to load the ITE firmware in order to prepare for traveling. The ITE firmware is made for use in places where strong encryption may be controlled or banned.
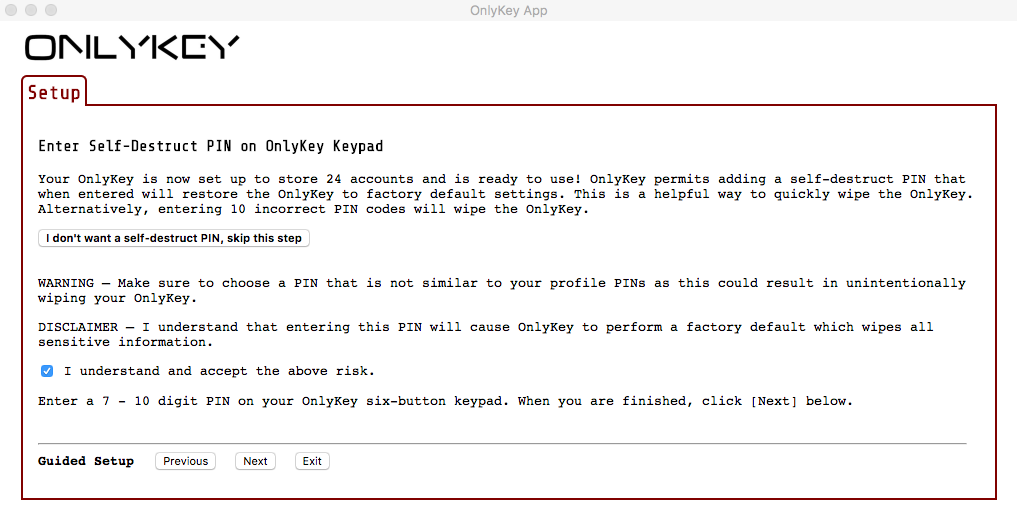
Q - Is having wipe mode set to “Full Wipe” an indicator that device is using plausible deniability?
A - We recommend that all users desiring the highest level of security enable full wipe. This is described in the user’s guide and in the International Travel Edition Guide as it ensures that no data or meta data such as what version of firmware was loaded is available to an adversary.
Q - Why not just give an adversary your self-destruct PIN?
A - If you are not concerned with plausible deniability then yes the self-destruct pin would be fine. The adversary would obviously know that this was intentional.
Q - Wouldn’t it be possible for an adversary to brute force the unknown primary profile PIN by trying 9 pins and then entering the known secondary profile pin?
A - When using a plausible deniability profile there is a counter that counts how many failed login attempts since the last primary profile login. You have a maximum of 20 failed attempts since the last successful login to the primary profile. Once that is reached the primary profile hash is deleted, essentially the primary profile is gone forever.